E-Learn Knowledge Base
Test-NetConnection: This versatile cmdlet tests network connectivity to a remote host, including ping, TCP port testing, and traceroute functionality.- Test-NetConnection -ComputerName "google.com" -Port 80 Test-NetConnection -ComputerName "192.168.1.1" -TraceRoute
Get-NetIPConfiguration: Displays detailed IP configuration information for all network adapters, including IP addresses, DNS servers, and default gateways.- Get-NetIPConfiguration
Get-NetAdapter: Provides information about network adapters on the system, including their status, speed, and MAC address.- Get-NetAdapter
Resolve-DnsName: Performs DNS lookups to resolve hostnames to IP addresses and vice-versa.
Get-NetRoute: Shows the IP routing table, indicating how network traffic is routed.Get-NetRoute
Get-NetAdapterStatistics: Provides statistics on network adapter activity, including sent and received packets.
- Get-NetAdapterStatistics -Name "Ethernet"
Get-NetTCPConnection: Displays information about active TCP connections on the system.- Get-NetTCPConnection
Get-DnsClientServerAddress: Retrieves the DNS server addresses configured for network adapters.
- Get-DnsClientServerAddress
Set-DnsClientServerAddress: Configures DNS server addresses for a specific network adapter.
- Set-DnsClientServerAddress -InterfaceAlias "Ethernet" -ServerAddresses ("8.8.8.8", "8.8.4.4")
Clear-DnsClientCache: Flushes the local DNS client cache.
- Clear-DnsClientCache
Get-NetFirewallProfile: Retrieves information about Windows Firewall profiles.
- Get-NetFirewallProfile
Get-NetTCPSetting: Retrieves TCP settings, which can be optimized for performance.
- Get-NetTCPSetting
Register for this course: Enrol Now
Introduction
Navigating the vast digital ocean of computer networks can seem daunting at first. Yet, just like a seasoned captain steering through seas with the help of a compass, we can navigate through this ocean using a set of tools. One such tool for Windows users is PowerShell, a command-line shell and scripting language that helps you manage and automate tasks on your machine. This article will walk you through some basic networking commands you can use in PowerShell to help you navigate your network more effectively.
1. Ping
The ping command is a basic yet essential networking command used to test the reachability of a host on an Internet Protocol (IP) network. It's like sending a hello message to a friend and waiting for a reply to know if they're available.
Here’s how you can use it:powershellCopy code
ping google.com
This command sends a small packet of information to Google’s servers, which then send a packet back. The roundtrip time is measured and displayed in the output.
2. ipconfig
ipconfig is a handy command that displays all current TCP/IP network configuration values and refreshes Dynamic Host Configuration Protocol (DHCP) and Domain Name System (DNS) settings. It's like asking your computer to spill the beans about its network setup.
Here’s how you can use it:powershellCopy code
ipconfig
If you want to get a fresh IP address from the DHCP server, you can use:powershellCopy code
ipconfig /renew
3. Get-NetIPAddress
Get-NetIPAddress is a powerful command that retrieves the IP addressing information from your computer. You can think of it as the digital equivalent of checking your home address.
Here’s how you can use it:powershellCopy code
Get-NetIPAddress
4. Test-NetConnection
Test-NetConnection is a cmdlet command that displays diagnostic information for a connection. It's like a doctor's checkup for your network, providing vital signs of your connection.
Here’s how you can use it:powershellCopy code
Test-NetConnection google.com
5. Resolve-DnsName
Resolve-DnsName is used to query Domain Name System (DNS) servers to resolve DNS names to IP addresses and vice versa. It's like looking up a phone number in a phone book using a person's name.
Here’s how you can use it:powershellCopy code
Resolve-DnsName google.com
6. Get-NetRoute
Get-NetRoute gets IP route information from the IP routing table. It's like checking a map to find the best route to your destination.
Here’s how you can use it:powershellCopy code
Get-NetRoute
7. netstat
The netstat command is a highly useful tool that displays active TCP connections, ports on which the computer is listening, Ethernet statistics, the IP routing table, and more. It's akin to taking a snapshot of all current network activities in your system.
Here’s how you can use it:powershellCopy code
netstat
8. tracert
The tracert command is a route tracing utility that displays the path that an IP packet has taken to reach a destination. It's like tracking a package from an online store, showing each 'hop' the package made to reach your doorstep.
Register for this course: Enrol Now
What is DNS and how does it work?
The Domain Name System (known as DNS) is a system used to convert a name (like www.google.com) into an IP address (like 192.168.2.1). These addresses are used by computers to communicate with each other on the internet. Most people find remembering names much easier than numbers, so DNS makes this process easy.
When you visit a website, your computer, phone or tablet will first check your local DNS cache for the corresponding IP address. If your device has not recently looked up this website, then it will need to ask your configured DNS server which will forward the request on to the DNS server responsible for managing the records. This process is known as a DNS lookup request.
Once the IP address is known, it is stored locally for a set period of time known as the Time To Live (TTL) and used to speed up future requests. Updated records will not be returned until this time has expired, this can often be the cause of why DNS changes do not appear to be working right away.
What is DNS propagation?
DNS propagation is the term commonly used to check the current state of DNS results globally and is often asked about when changes made to DNS zones do not appear to be working as expected. This process can take from only a few minutes, but often takes up to 48-72 hours and sometimes longer.
While technically DNS does not propagate, this is the term that people have become familiar with. DNS requests are recursively forwarded and looked up from the locally used resolver to the authoritative name server on demand and then cached to speed up future lookup requests. For this reason, commonly used DNS servers of large network providers located around the world have been selected when performing DNS checks.
For popular websites, DNS results may be cached for people in different parts of the world using many different recursive DNS resolvers. If you have recently made changes to your configuration, and the TTL has not yet expired, then some people may be receiving out of date results which could mean that they see an older version of your website.
How long does DNS propagation take?
How long DNS propagation takes usually depends on your records TTL setting. This can be anywhere from several minutes up to 48-72 hours or longer. However, there are sometimes other reasons for a long propagation time.
The main issues as to why DNS propagation can take so long are:
DNS Cache - The Time to Live (TTL) is the duration in which DNS data is allowed to 'live' in the cache of a local device or DNS resolver. When this duration expires, the local device or server removes existing DNS information and carries out another DNS lookup to fetch new information. Higher TTL settings can often cause a delay in DNS propagation.
Internet Service Providers - Your ISP also caches DNS results, which allows for many users to access sites faster. For every website requested, they will ask the DNS server responsible only once but return the same result for many users. Some ISPs also overlook TTL rules, keeping a cached DNS record even if the TTL has expired. This can make DNS propagation take longer than it should.
Other DNS Servers - You may not be using your ISPs DNS server, if this is the case then the same issues that may be causing delays can still apply.
Domain Name Registrar - When changing web hosting or DNS providers for your domain, it is often also required to update your authoritative name servers. These changes will need to be reflected in the corresponding TLD nameserver for your domain name. For example, if you were to change the NS records for example.com, then the .com TLD nameserver would also need to update which can cause delays in DNS propagation.
How do you speed up DNS propagation?
A technique used to speed up DNS propagation and prevent a delay is to lower your DNS records TTL a few days in advance of making any changes so that when the change is made any old records expire more quickly. Unfortunately, most people who are having issues and trying to speed up DNS propagation only find this out after making changes and are wondering why they're not seeing instant results.
If you have checked DNS globally, and are seeing different results locally then you may consider flushing your DNS cache, or using another DNS server. As a last resort, manually overriding your local DNS entries in your systems hosts file can also be done but should be considered a temporary measure and only works for certain record types.
What server types are used in a DNS check?
There are 4 different types of DNS servers involved when performing a DNS check. Each has a different role and may not be needed at all depending on the situation, having all these different server types is what contributes to DNS propagation issues.
Recursive Resolver - The DNS server your device communicates with is called the recursive resolver and is issued to you automatically by your ISP, but can be also configured on your router or individual devices. These DNS severs are ideally located in close geographical proximity to return results as fast as possible. These servers will cache a copy of the DNS results to speed up future DNS lookup requests.
Root Name Server - This type of DNS server is responsible for returning the IP address of the TLD (Top Level Domain) nameserver. For instance, if it is trying to resolve example.com, the root name server returns the IP of the TLD name server that runs .com domains.
TLD Name Server - This name server returns the authoritative name servers for each domain under the Top Level Domain it's responsible for. The .com TLD name server will return results for example.com but not example.org.
Authoritative Name Server - This stores DNS servers' configuration data for specific domain names.
What happens when a DNS request is made?
Below demonstrates the flow of events when a user requests to visit www.example.com in their web browser for the first time and does not yet have cached results. As you can see, each step introduces the possibility of a DNS propagation delay.
- → You type
www.example.cominto your web browser. - → Your device sends a request to your configured recursive resolver.
- → The recursive resolver asks the root nameserver for the IP address of the TLD nameserver responsible for
.comdomains. - ← The root nameserver returns the IP address of the .com TLD nameserver to the recursive resolver.
- → The recursive resolver asks the .com TLD nameserver for the address of the authoritative nameserver responsible for
example.com. - ← The .com TLD nameserver returns the IP address of the authoritative nameserver to the recursive resolver.
- → The recursive resolver asks the authoritative nameserver for the IP address of
www.example.com. - ← The authoritative nameserver returns the IP address of
www.example.comto the recursive resolver. - ← The recursive resolver returns IP address of
www.example.comto the browser. - → Your browser makes a web request directly to the resolved IP address.
Which DNS record types can be checked?
You can check DNS propagation for common record types including:
- A - The most common DNS record, used to point a domain to an IP address.
- CNAME - Also known as alias records, they point to other DNS records. Sometimes used for subdomains like www.
- MX - Mail Exchanger records are used set email servers and their priority.
- NS - Name Server records store the authoritative nameserver.
- TXT - Text records are commonly used for configuration settings such as SPF and DKIM records.
Additional types that can be checked which are usually used in more advanced configurations include: AAAA, CAA, PTR, SOA and SRV.
Authors: T. C. OkennaRegister for this course: Enrol Now
What Are the Differences Between Multicast and Unicast?
Multicast and unicast are both packet transmission modes.
Unicast is a mode of one-to-one communication between hosts. In this mode, each device selects a transmission path to the destination address included in each received packet and forwards the packet accordingly without copying the packet. Unicast ensures that each host is responded to quickly. Currently, Internet browsing uses the unicast mode.
Multicast on the other hand enables one-to-many communication among hosts. It enables one or more multicast sources to send one copy of a packet to multiple receivers. The packet is sent to a specific multicast address, which, unlike unicast addresses, belongs to a group of hosts rather than a single host. To receive the multicast packet, a host must join the multicast group to which the packet is sent.
On the network illustrated in the figure, if unicast is used, the destination address of each data packet must be a unicast address, and the data source needs to send a copy of the packet to each receiver. If unicast is used to send packets to multiple receivers in the network, the data source needs to send a copy of the packet to each receiver individually. If multicast is used, a multicast address is used as the destination address, and the data source sends only one copy of a packet to the multicast group even if multiple receivers require the packet.
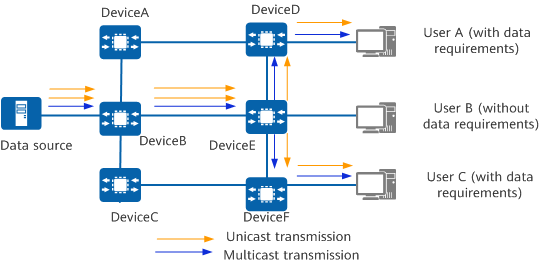
Comparison between multicast and unicast transmission modes
Unicast is applicable to networks with a small number of users. If unicast is used on a network with a large number of users, duplicate packet copies will be transmitted on the network, consuming a large number of processor resources and excessive amount of network bandwidth. If multicast is used, each link on the network has only one data flow (without duplicate packet copies). The advantage of multicast over unicast is that each link has at most one copy of the same packet.
What Are the Differences Between Multicast and Broadcast?
Multicast and broadcast are both packet transmission modes.
Broadcast is a mode of one-to-all communication among hosts. When this mode is used, each device copies received broadcast packets and forwards them to all possible receivers on the network through all interfaces except the inbound interface. The broadcast process is simple, and path selection is not involved.
Multicast on the other hand enables one-to-many communication among hosts. It enables one or more multicast sources to send one copy of a packet to multiple receivers.
On the network shown in the figure, if broadcast is used, a broadcast address must be used as the destination address of each data packet, and the data source sends only one copy of a packet to the broadcast IP address corresponding to the local network segment. The packet copy is then sent to all users on the local network segment, regardless of whether the users have data requirements. If multicast is used, data packets are sent only to the users who require them rather than to all users.
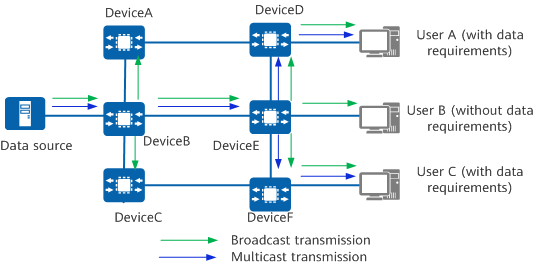
Comparison between multicast and broadcast transmission modes
Broadcast requires that the data source and users be on the same network segment, whereas multicast enables data to be transmitted across network segments. When broadcast is used, all hosts on the network segment can receive data packets, regardless of whether they have data requirements. In this case, there will be redundant traffic on the network. When multicast is used, data packets are transmitted only to the users who require them, and there is no redundant traffic on the network. Compared with broadcast, multicast has the advantage of on-demand packet forwarding.
Range of IP Multicast Addresses
IP multicast addresses used by network-layer multicast are required to enable multicast sources and group members to communicate.
IPv4 multicast addresses
The Internet Assigned Numbers Authority (IANA) allocates Class D address space to IPv4 multicast. An IPv4 address is 32 bits long, and the four most significant bits of a Class D address is 1110. The IPv4 multicast address ranges from 224.0.0.0 to 239.255.255.255. The following figure elaborates on IPv4 multicast addresses.
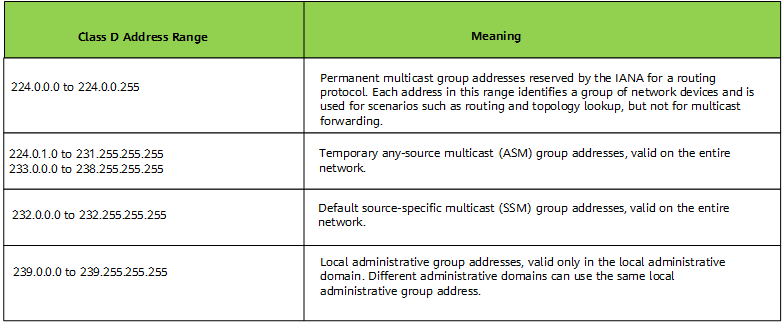
Ranges and meanings of IPv4 multicast addresses
IPv6 multicast addresses
An IPv6 address is 128 bits long. The following figure illustrates the format of an IPv6 multicast address.
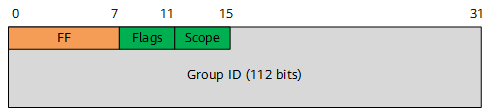
IPv6 multicast address format
- An IPv6 multicast address always starts with FF, and the eight most significant bits are 11111111.
- The Flags field is 4 bits long and indicates the state of a multicast address. For example, the value 0 indicates a reserved group address, the value 1 or 2 indicates a multicast address in the ASM group address range, and the value 3 indicates a multicast address in the SSM group address range.
-
The Scope field is 4 bits long and indicates the application scope of a multicast group (whether a multicast group covers nodes in the same network, same site, same organization or any node in the global address space).
- The Group ID field is 112 bits long and indicates a multicast group in the range specified by the Scope field.
The following figure describes the ranges and meanings of fixed IPv6 multicast addresses.
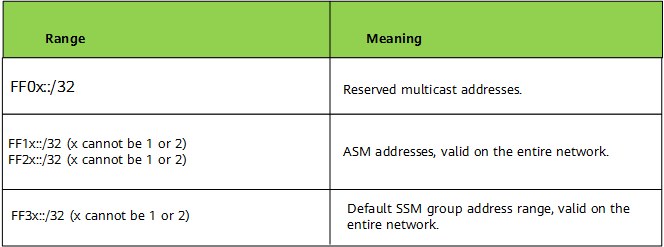
Ranges and meanings of IPv6 multicast addresses
Range of Multicast MAC Addresses
To enable multicast data to be correctly transmitted on the local physical network, multicast MAC addresses must be used at the link layer. The destination address of multicast data indicates a group of members (of which the multicast source is unaware) rather than a specific receiver. Therefore, IP multicast addresses must be mapped to multicast MAC addresses.
IPv4 multicast MAC addresses
When IPv4 unicast packets are transmitted on an Ethernet network, they use the receivers' MAC addresses as destination MAC addresses. However, the destination of a multicast data packet indicates a group of members (of which the multicast source is unaware) rather than a specific receiver. Therefore, multicast data packets must use IPv4 multicast MAC addresses, which are link-layer addresses mapped from IPv4 multicast addresses.
As defined by the IANA, the 24 most significant bits of an IPv4 multicast MAC address are 0x01005e, the 25th bit is 0, and the 23 least significant bits are the same as the 23 least significant bits of an IPv4 multicast address, as shown in the figure. For example, the multicast MAC address corresponding to the IP multicast address 224.0.1.1 is 01-00-5e-00-01-01.
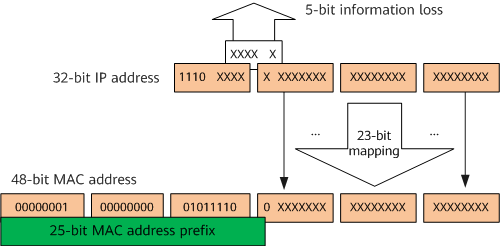
Mapping between an IPv4 multicast address and an IPv4 multicast MAC address
The four most significant bits of an IPv4 multicast address are fixed at 1110, mapping the 25 most significant bits of a multicast MAC address. Among the last 28 bits, only 23 bits are mapped to a MAC address, and 5 bits are lost. As a result, 32 IPv4 multicast addresses are mapped to the same MAC address. For example, IP multicast addresses 224.0.1.1, 224.128.1.1, 225.0.1.1, and 239.128.1.1 are all mapped to the multicast MAC address 01-00-5e-00-01-01.
IPv6 multicast MAC addresses
In an IPv6 multicast MAC address, the 16 most significant bits are 0x3333 and the 32 least significant bits are mapped to the 32 least significant bits of an IPv6 multicast address. The following figure shows the mapping between an IPv6 multicast address and MAC address.
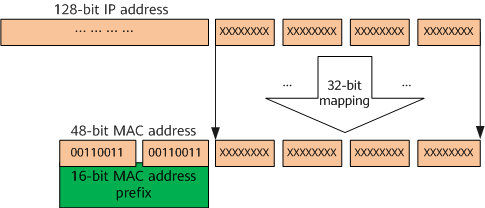
Mapping between an IPv6 multicast address and MAC address
It can be seen from the preceding figure that more IPv6 multicast addresses are mapped to the same multicast MAC address.
What Are the Common Multicast Protocols?
In the IP multicast transmission model, the sender only needs to send data to a specified destination address and does not need to know the receivers' locations. The remaining forwarding work is performed by the network. Multicast devices on the network must collect information about the receivers, and replicate and forward multicast packets along the correct paths. During multicast development, a complete set of protocols are established to implement multicast.
Multicast protocols used on an IPv4 network
- Internet Group Management Protocol (IGMP)
IGMP manages IPv4 multicast group members and runs on the multicast network's last segment (that is, the network segment where a Layer 3 network device is connected to user hosts). Hosts use IGMP to join or leave multicast groups, and upstream Layer 3 multicast devices use IGMP to manage and maintain group memberships. IGMP can exchange information with upper-layer multicast routing protocols.
- Protocol Independent Multicast (PIM)
PIM is a multicast routing protocol used on an IPv4 network to forward multicast data to the multicast device connected to group members that have requested the multicast data. This implements multicast data forwarding based on routes.
PIM works in sparse mode (PIM-SM) or dense mode (PIM-DM). PIM-SM is applicable to large-scale networks with sparsely distributed group members, whereas PIM-DM is applicable to small-scale networks with densely distributed group members.
- Multicast Source Discovery Protocol (MSDP)
MSDP is an inter-domain multicast protocol developed for interconnection among multiple PIM-SM domains. It is used to discover multicast source information in other PIM-SM domains and send information about active sources in other PIM-SM domains to receivers in the local domain. This implements inter-domain multicast packet forwarding.
- Multiprotocol Border Gateway Protocol (MBGP)
MBGP implements inter-AS multicast forwarding. It is applicable to scenarios where multicast sources and receivers are in different ASs.
- IGMP snooping
IGMP snooping enables a device working at Layer 2 to establish a Layer 2 multicast forwarding table by listening to IGMP messages exchanged between the upstream Layer 3 device and user hosts. The device working at Layer 2 manages and controls the forwarding of multicast data packets based on the Layer 2 multicast forwarding table, suppressing multicast data flooding on the Layer 2 network.
- Bit Index Explicit Replication (BIER)
BIER is a multicast technology. It encapsulates a set of destination nodes of multicast packets in a BitString in the packet header before sending the packets. With BIER enabled, transit nodes do not need to establish an MDT for each multicast flow, or maintain the states of multicast flows. Instead, the transit nodes replicate and forward packets according to the BitString in the packet header.
Multicast protocols used on an IPv6 network
- Multicast Listener Discovery (MLD)
MLD manages IPv6 multicast group members and runs on the multicast network's last segment (that is, the network segment where a Layer 3 multicast device is connected to user hosts). Hosts use MLD to join or leave multicast groups, and Layer 3 multicast devices use MLD to manage and maintain group memberships. MLD can exchange information with multicast routing protocols.
- IPv6 PIM
IPv6 PIM is a multicast routing protocol used on an IPv6 network to forward multicast data to the multicast device connected to group members that have requested the multicast data. This implements multicast data forwarding based on routes.
IPv6 PIM works in sparse mode (IPv6 PIM-SM) or dense mode (IPv6 PIM-DM). IPv6 PIM-SM applies to large-scale networks with sparsely distributed group members, and IPv6 PIM-DM applies to small-scale networks with densely distributed group members.
- MLD snooping
MLD snooping enables a device working at Layer 2 to establish an IPv6 Layer 2 multicast forwarding table by listening to MLD messages exchanged between the upstream Layer 3 device and user hosts. The device working at Layer 2 manages and controls the forwarding of multicast data packets based on the Layer 2 multicast forwarding table, suppressing multicast data flooding on the Layer 2 network.
- BIERv6
BIERv6 inherits the advantages of BIER and uses IPv6 scalability to implement new applications of multicast routing technologies on IPv6 networks. It is easy to deploy, intelligent, and highly reliable.
Register for this course: Enrol Now
IP addresses: Networks and hosts
An IP address is a 32-bit number. It uniquely identifies a host (computer or other device, such as a printer or router) on a TCP/IP network.
IP addresses are normally expressed in dotted-decimal format, with four numbers separated by periods, such as 192.168.123.132. To understand how subnet masks are used to distinguish between hosts, networks, and subnetworks, examine an IP address in binary notation.
For example, the dotted-decimal IP address 192.168.123.132 is (in binary notation) the 32-bit number 11000000101010000111101110000100. This number may be hard to make sense of, so divide it into four parts of eight binary digits.
These 8-bit sections are known as octets. The example IP address, then, becomes 11000000.10101000.01111011.10000100. This number only makes a little more sense, so for most uses, convert the binary address into dotted-decimal format (192.168.123.132). The decimal numbers separated by periods are the octets converted from binary to decimal notation.
For a TCP/IP wide area network (WAN) to work efficiently as a collection of networks, the routers that pass packets of data between networks don't know the exact location of a host for which a packet of information is destined. Routers only know what network the host is a member of and use information stored in their route table to determine how to get the packet to the destination host's network. After the packet is delivered to the destination's network, the packet is delivered to the appropriate host.
For this process to work, an IP address has two parts. The first part of an IP address is used as a network address, the last part as a host address. If you take the example 192.168.123.132 and divide it into these two parts, you get 192.168.123. Network .132 Host or 192.168.123.0 - network address. 0.0.0.132 - host address.
Subnet mask
The second item, which is required for TCP/IP to work, is the subnet mask. The subnet mask is used by the TCP/IP protocol to determine whether a host is on the local subnet or on a remote network.
In TCP/IP, the parts of the IP address that are used as the network and host addresses aren't fixed. Unless you have more information, the network and host addresses above can't be determined. This information is supplied in another 32-bit number called a subnet mask. The subnet mask is 255.255.255.0 in this example. It isn't obvious what this number means unless you know 255 in binary notation equals 11111111. So, the subnet mask is 11111111.11111111.11111111.00000000.
Lining up the IP address and the subnet mask together, the network, and host portions of the address can be separated:
11000000.10101000.01111011.10000100 - IP address (192.168.123.132)
11111111.11111111.11111111.00000000 - Subnet mask (255.255.255.0)
The first 24 bits (the number of ones in the subnet mask) are identified as the network address. The last 8 bits (the number of remaining zeros in the subnet mask) are identified as the host address. It gives you the following addresses:
11000000.10101000.01111011.00000000 - Network address (192.168.123.0)
00000000.00000000.00000000.10000100 - Host address (000.000.000.132)
So now you know, for this example using a 255.255.255.0 subnet mask, that the network ID is 192.168.123.0, and the host address is 0.0.0.132. When a packet arrives on the 192.168.123.0 subnet (from the local subnet or a remote network), and it has a destination address of 192.168.123.132, your computer will receive it from the network and process it.
Almost all decimal subnet masks convert to binary numbers that are all ones on the left and all zeros on the right. Some other common subnet masks are:
| Decimal | Binary |
|---|---|
| 255.255.255.192 | 1111111.11111111.1111111.11000000 |
| 255.255.255.224 | 1111111.11111111.1111111.11100000 |
Internet RFC 1878 describes the valid subnets and subnet masks that can be used on TCP/IP networks.
Network classes
IP addresses are allocated by the InterNIC, the organization that administers the Internet. These IP addresses are divided into classes. The most common of them are classes A, B, and C. Classes D and E exist, but aren't used by end users. Each of the address classes has a different default subnet mask. You can identify the class of an IP address by looking at its first octet. Following are the ranges of Class A, B, and C IP addresses, each with an example address:
-
Class A networks use a default subnet mask of 255.0.0.0 and have 0-127 as their first octet. The address 10.52.36.11 is a class A address. Its first octet is 10, which is between 0 and 127, inclusive.
-
Class B networks use a default subnet mask of 255.255.0.0 and have 128-191 as their first octet. The address 172.16.52.63 is a class B address. Its first octet is 172, which is between 128 and 191, inclusive.
-
Class C networks use a default subnet mask of 255.255.255.0 and have 192-223 as their first octet. The address 192.168.123.132 is a class C address. Its first octet is 192, which is between 192 and 223, inclusive.
In some scenarios, the default subnet mask values don't fit the organization needs for one of the following reasons:
- The physical topology of the network
- The numbers of networks (or hosts) don't fit within the default subnet mask restrictions.
The next section explains how networks can be divided using subnet masks.
Subnetting
A Class A, B, or C TCP/IP network can be further divided, or subnetted, by a system administrator. It becomes necessary as you reconcile the logical address scheme of the Internet (the abstract world of IP addresses and subnets) with the physical networks in use by the real world.
A system administrator who is allocated a block of IP addresses may be administering networks that aren't organized in a way that easily fits these addresses. For example, you have a wide area network with 150 hosts on three networks (in different cities) that are connected by a TCP/IP router. Each of these three networks has 50 hosts. You are allocated the class C network 192.168.123.0. (For illustration, this address is actually from a range that isn't allocated on the Internet.) It means that you can use the addresses 192.168.123.1 to 192.168.123.254 for your 150 hosts.
Two addresses that can't be used in your example are 192.168.123.0 and 192.168.123.255 because binary addresses with a host portion of all ones and all zeros are invalid. The zero address is invalid because it's used to specify a network without specifying a host. The 255 address (in binary notation, a host address of all ones) is used to broadcast a message to every host on a network. Just remember that the first and last address in any network or subnet can't be assigned to any individual host.
You should now be able to give IP addresses to 254 hosts. It works fine if all 150 computers are on a single network. However, your 150 computers are on three separate physical networks. Instead of requesting more address blocks for each network, you divide your network into subnets that enable you to use one block of addresses on multiple physical networks.
In this case, you divide your network into four subnets by using a subnet mask that makes the network address larger and the possible range of host addresses smaller. In other words, you are 'borrowing' some of the bits used for the host address, and using them for the network portion of the address. The subnet mask 255.255.255.192 gives you four networks of 62 hosts each. It works because in binary notation, 255.255.255.192 is the same as 1111111.11111111.1111111.11000000. The first two digits of the last octet become network addresses, so you get the additional networks 00000000 (0), 01000000 (64), 10000000 (128) and 11000000 (192). (Some administrators will only use two of the subnetworks using 255.255.255.192 as a subnet mask. For more information on this topic, see RFC 1878.) In these four networks, the last six binary digits can be used for host addresses.
Using a subnet mask of 255.255.255.192, your 192.168.123.0 network then becomes the four networks 192.168.123.0, 192.168.123.64, 192.168.123.128 and 192.168.123.192. These four networks would have as valid host addresses:
192.168.123.1-62 192.168.123.65-126 192.168.123.129-190 192.168.123.193-254
Remember, again, that binary host addresses with all ones or all zeros are invalid, so you can't use addresses with the last octet of 0, 63, 64, 127, 128, 191, 192, or 255.
You can see how it works by looking at two host addresses, 192.168.123.71 and 192.168.123.133. If you used the default Class C subnet mask of 255.255.255.0, both addresses are on the 192.168.123.0 network. However, if you use the subnet mask of 255.255.255.192, they are on different networks; 192.168.123.71 is on the 192.168.123.64 network, 192.168.123.133 is on the 192.168.123.128 network.
Default gateways
If a TCP/IP computer needs to communicate with a host on another network, it will usually communicate through a device called a router. In TCP/IP terms, a router that is specified on a host, which links the host's subnet to other networks, is called a default gateway. This section explains how TCP/IP determines whether or not to send packets to its default gateway to reach another computer or device on the network.
When a host attempts to communicate with another device using TCP/IP, it performs a comparison process using the defined subnet mask and the destination IP address versus the subnet mask and its own IP address. The result of this comparison tells the computer whether the destination is a local host or a remote host.
If the result of this process determines the destination to be a local host, then the computer will send the packet on the local subnet. If the result of the comparison determines the destination to be a remote host, then the computer will forward the packet to the default gateway defined in its TCP/IP properties. It's then the responsibility of the router to forward the packet to the correct subnet.
Troubleshooting
TCP/IP network problems are often caused by incorrect configuration of the three main entries in a computer's TCP/IP properties. By understanding how errors in TCP/IP configuration affect network operations, you can solve many common TCP/IP problems.
Incorrect subnet mask
If a network uses a subnet mask other than the default mask for its address class, and a client is still configured with the default subnet mask for the address class, communication will fail to some nearby networks but not to distant ones.
As an example, if you create four subnets (such as in the subnetting example) but use the incorrect subnet mask of 255.255.255.0 in your TCP/IP configuration, hosts won't be able to determine that some computers are on different subnets than their own. In this situation, packets destined for hosts on different physical networks that are part of the same Class C address won't be sent to a default gateway for delivery.
A common symptom of this issue is when a computer can communicate with hosts that are on its local network and can talk to all remote networks except those networks that are nearby and have the same class A, B, or C address. To fix this problem, just enter the correct subnet mask in the TCP/IP configuration for that host.
Incorrect IP address
If you put computers with IP addresses that should be on separate subnets on a local network with each other, they won't be able to communicate. They'll try to send packets to each other through a router that can't forward them correctly. A symptom of this problem is a computer that can talk to hosts on remote networks but can't communicate with some or all computers on their local network.
To correct this problem, make sure all computers on the same physical network have IP addresses on the same IP subnet. If you run out of IP addresses on a single network segment, there are solutions that go beyond the scope of this article.
Incorrect default gateway
A computer configured with an incorrect default gateway can communicate with hosts on its own network segment. But it will fail to communicate with hosts on some or all remote networks. A host can communicate with some remote networks but not others if the following conditions are true:
- A single physical network has more than one router.
- The wrong router is configured as a default gateway.
This problem is common if an organization has a router to an internal TCP/IP network and another router connected to the Internet.
Authors: T. C. OkennaRegister for this course: Enrol Now
